Writeup BreizhCTF 2022 - Turn your wifi off !
Description:
# Turn your wifi off !
Value: 383
Description:
Un téléphone à proximité a le wifi d'allumé, peux-tu regarder les réseaux où il s'est connecté auparavant ?
Auteur: LaChenilleBarbue
Format : BZHCTF{information}First thoughts
The description is talking about Wi-Fi and challenge title is telling us to find the Wi-Fi name a device is trying to connecting to. Since the challenge is flagged as easy, we can think of sniffing the probe requests in order to get the flag.
This challenge is pretty easy, I will therefore make it look like a tutorial for how to get started into "Wi-Fi hacking".
But first, what is a probe request?
Wi-Fi probe request
When a device is searching for a Wi-Fi hotspot, there is 2 options:
- Waiting the hotspot to broadcast a probe response by itself, it's called passive scanning
- Broadcasting a probe request (wich contains Wi-Fi SSID) and wait for a probe response from the hotspot, it's called Active scanning
Since those probe requests aren't encrypted of any sort, everyone can see them. Here's a quick schema of what it actually looks like:
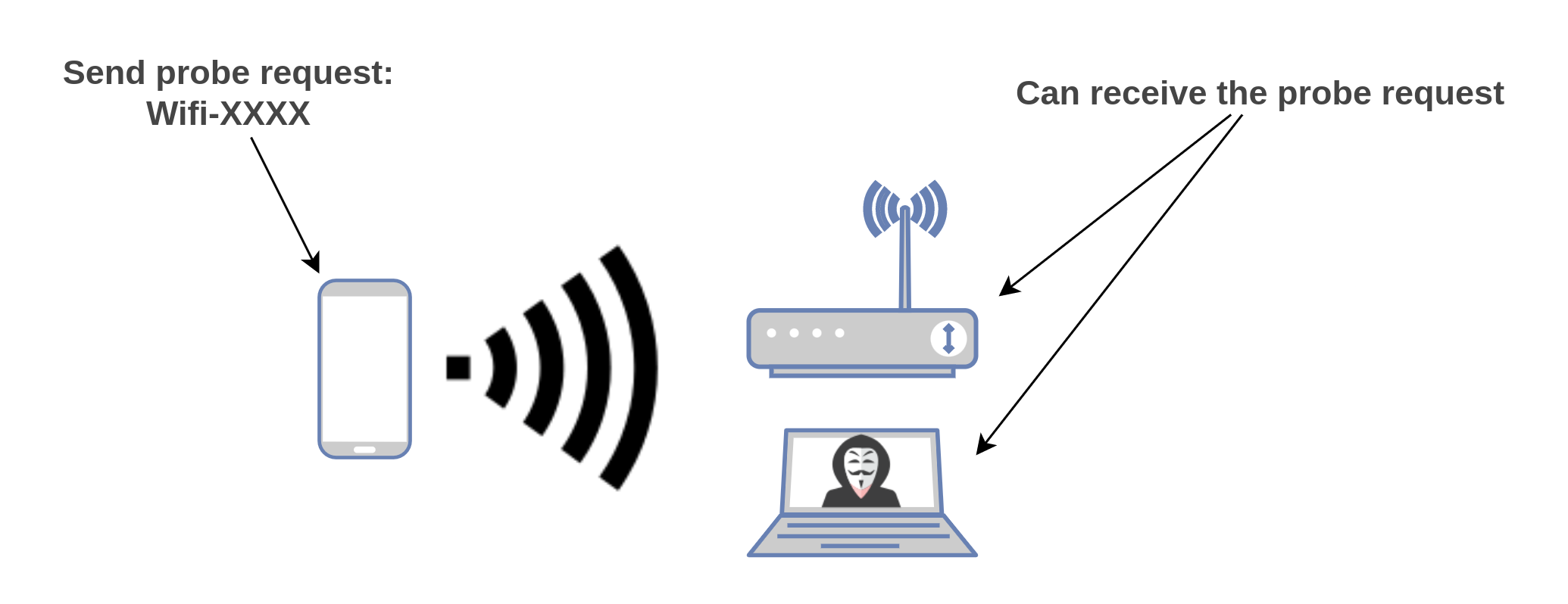
© my poor design skills (feel free to reuse)
As you can see, every person in the range of the signal can catch the probe request and thus get the SSID of the requested Wi-Fi hotspot.
Exploitation
In order to catch those requests, we are going to use the airmon-ng utility and a Wi-Fi card.
We first need to get the associated interface of our Wi-Fi card:
$ ip a
...
8: wlp4s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether xx:xx:xx:xx:xx:xx brd ff:ff:ff:ff:ff:ff
...The interface name is wlp4s0. We can now start airmon-ng on this interface and then use airodump-ng to catch probe requests:
$ sudo airmon-ng start wlp4s0
$ sudo airodump-ng wlp4s0mon
# To stop `airmon-ng` and get your Wi-Fi back, you can use this command:
$ sudo airmon-ng stop wlp4s0mon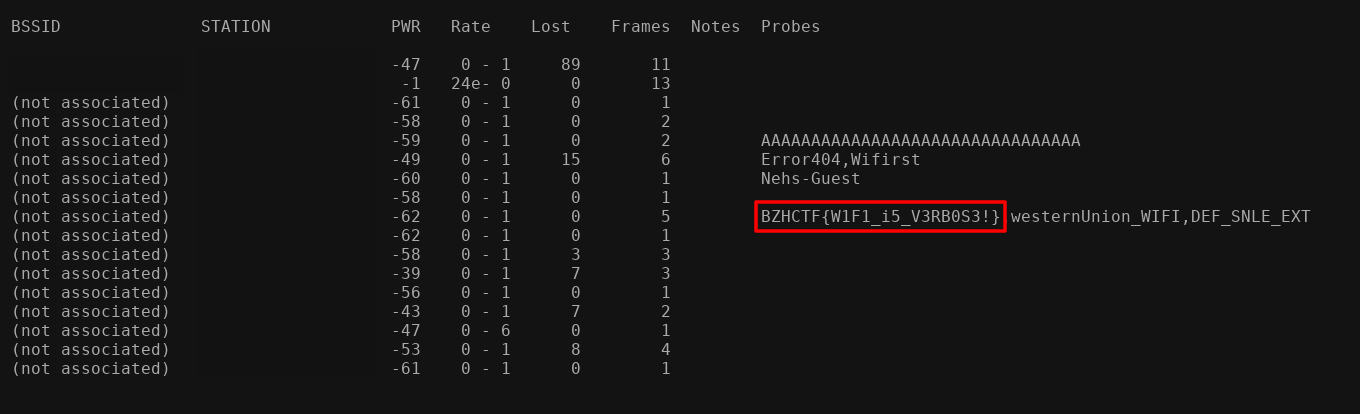
After waiting a few seconds, we can see Wi-Fi SSID appears, and there is one that look like our flag!
Flag: BZHCTF{W1F1_i5_V3RB0S3!}